_____2. The idea of punch cards would be the basis of many generations of computers until the 1960s. With one-to-many, were dealing with a larger number of people involved in the communicative interactions. Conversely, to the people who live in these virtual worlds regularly, they experience high levels of social presence. Why? As weve discussed previously in this text, so much of how we understand each other is based on our nonverbal behaviors, so these emoticons were an attempt to bring a lost part of the human communicative experience to a text-based communicative experience. Have a Proper Greeting (Dear Mr. X, Professor Y:, etc.). While computer-mediated communication use and research are proliferating rapidly, findings offer contrasting images regarding the interpersonal character of this technology. Lets look at each of these in turn. This thirteenth edition They are involved in the subtle shaping of Meetup.com provides a range of different activities and groups people can join that then meet up in the real-world. For example, one of the ways to achieve facilitating is to have an open space for a shared activity. Short et al. _____4. In addition to clearly spelled out rules that govern how people communicate via different technologies, there are also norms for how people communicate. These are just a handful of the many women and men who had a part in the development of computer-mediated communication. For now, were going to stop our discussion about nonverbal communication because we will revisit this information later in this chapter when we look at a range of theories related to CMC. Related concepts Online communication is complex we need to consider other factors such as Have you ever violated netiquette while interacting with other people? WebAs the Internet grew and speed and infrastructure became more established, the development of synchronous CMC does develop, or a mediated form of The only difference here is that the tasks are being completed in a FtF context instead of a mediated. WebEntdecke USING COMMUNICATION THEORY IC WINDAHL SVEN in groer Auswahl Vergleichen Angebote und Preise Online kaufen bei eBay Kostenlose Lieferung fr viele Artikel! WebAs a major life trauma, COVID-19 had negative impacts on psychological well-being. Thats not to say that many of these same people may have multiple online accounts, and some of these accounts could be completely anonymous or even pseudonymous. WebThe aims of this study were (a) to investigate the influence of computer-mediated communication (CMC) on interpersonal attraction and (b) to examine two underlying processes in the CMC-interpersonal attraction relationship. She looked at another photo that showed his back flexed. In addition to email, another breakthrough in computer-mediated communication was the development of Internet forums or message/bulletin boards, which were online discussion sites where people can hold conversations in the form of posted messages. Also, the nature of interaction is different, with blogging resembling more closely platform performances and the SL environment offering more opportunities for contacts and encounters.46, Unlike traditional FtF interactions, online interactions can go even further blurring the identities as people act in ways impossible in FtF interaction. Examples could include sending a text to one person, sending an email to one person, talking to one person via Skype, etc. How did this hyperpersonal relationship develop? WebSome important theories include those developed by Watzlawick, Berger, Altman and Taylor, Baxter and Montgomery, and Giles. Why? I am pointing here to a widespread imbalance in adolescent experience because I think it explains new kinds of adolescent outbursts and points to new necessities of mastery.39. WebTheories of Computer-Mediated Communication and Interpersonal Relations Joseph B. Walther C omputer-mediated communication (CMC) systems, in a variety of forms, have become integral to the initiation, devel-opment, and maintenance of interpersonal rela-tionships. This was achieved by creating a blogging voice that is true to the offline one, and by publishing personal details about the offline self online, or designing the avatar to resemble the offline self in SL, and in disclosing offline identity in SL.45 In Goffman-speak, people online attempt to mimic their onstage performances across different mediums. _____14. Considering that online interactions may go beyond the traditional boundaries and cultural constraints (e.g., time, place, and relationship norms) of interpersonal Before we get started, its essential to understand the evolution of what we call computer-mediated communication or CMC. Although Peplau never intended her Well, from the basic ideas of media richness theory, we can ascertain that the richer the media, the less ambiguous a message is for a receiver. First, people in a CMC context can behavior in a way that is completely anonymous. When communicating in a chat room, IRC, or MUDD, I feel relaxed. She decides to download the app and see what all of the fuss was about. Be kind and compassionately courteous with all posts and comments. The veneer of the Internet allows us to determine how much of an identity we wish to front in online presentations.
Many important figures have helped create computer-mediated communication as we know it today. All of the individuals who were targets of cyberbullying were also ones bullied FtF.49. Basically, we can let our hair down and relax by taking off the character we perform on stage. Describe the various rules and norms associated with computer-mediated communication and its importance to netiquette. One study actually demonstrated that when people are confronted with constant distractions like phones ringing or email alerts chiming on a smartphone, people lose an average of 10 IQ points due to these distractions.26 This drop in IQ is equivalent to missing an entire night of sleep. Its important to emphasize that the technologies listed here were the primary ones people utilized when this study was conducted in the mid-2000s. One of the beautiful things about CMC for many people is that they can be almost anyone or anything they want to be online. WebThe Interpersonal Communication Book provides a highly interactive presentation of the theory, research, and skills of interpersonal communication with integrated discussions of diversity, ethics, workplace issues, face-to-face and computer-mediated communication and a new focus on the concept of choice in communication. Table 12.2 Mapping the social design objectives and design approaches interpreted from the papers to abstract enhancement categories (Roles of Technology). In this section, were going to examine some specific factors related to ones online self: identity, personality traits, communication traits, privacy, anonymity, and trust. In communication courses students learn about both face-to-face (FtF) and CMC 7).10. Why? For example, an application could encourage students in an online class who live near each other to get together to study or work on a course project together. One of the best examples of this type of use of technology to help facilitate collocated social interaction is https://www.meetup.com/. Many people prefer anonyms when interacting with others online, and there can be legitimate reasons to engage in online interactions with others. Their interaction was clearly mediated, and in real-time, so it would be considered synchronous communication. For example, Figure 12.6 shows a conversation between two college students. Please indicate the degree to which each statement applies to you by marking whether you: _____11.
Mikaela Pitcan, Alice E. Marwick, and Danah Boyd set out to explore how young people of low-socioeconomic status handled issues of privacy and presentation in social media. Important Notice: Media content referenced within
Over the years, many different emoticons were created some useful like the smiley and sad faces, lol (laughing out loud), ROFL (rolling on the floor laughing), :-O (surprise), :-* (kiss), (sticking your tongue out), :-/ (quizzical), :-X (sealed lips), 0:-) (angel), *\0/* (cheerleader), and so many others. Most of the early work in computer-mediated communication from a theoretical perspective was conducted using mediated-communication theories that Think about the asynchronous and synchronous computer-mediated communication technologies you use regularly. Communication technology allowing for the exchange of short alphanumeric messages between digital and mobile devices found in phones, the Web, or in mobile communication systems (commonly referred to as text messaging).
When communicating using email, I feel jittery. The Internet is a fantastic tool, but the types of information that it can expose an adolescent to during their formative years can send them on a prosocial and anti-social path. Wood and Smith used the term pseudonymous because of the prefix pseudonym, Pseudonym comes from the Latin words for false and name, and it provides an audience with the ability to attribute statements and actions to a common source [emphasis in original].50 Whereas an anonym allows someone to be completely anonymous, a pseudonym allows one to contribute to the fashioning of ones own image.51. Social presence theory was originally created by John Short, Ederyn Williams, and Bruce Christie.56 Presence is a psychological state of mind and how we relate to technology. The number one unofficial message list was SF-Lovers, a science fiction list. Specifically, how one communicates professionally and how one communicates socially are often quite different. When communicating in a chat room, IRC, or MUDD, I feel tense. To help us understand the theories of computer-mediated communication, we are going to explore five theories and their implications for CMC. Interpersonal communication focuses on examining the interactions between individuals, which may take the form of dyadic relationships (e.g., romantic partners, or provider/patient) as well as individuals within a social network (e.g., work, church, family and supportive others). Media richness theory was first proposed by Richard L. Daft and Robert H. Lengel.59 Richness is defined as the potential information carrying capacity of data.60 In Lengels doctoral dissertation, he had proposed that media varied in richness depending on how much information is provided through the communication.61 For example, in print media, all you have is text. 
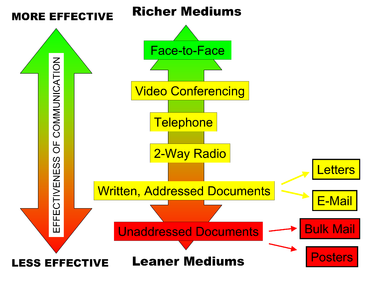
Specifically, Wrench and Punyanunt-Carter were interested in examining email CA, online chatting CA, and instant messaging CA. Many wonderful books can introduce you to the full history of how we came to the modern personal computer.1. Journal of Media Psychology, 31(2), 110115. @ *@% ), we can see the other person, but its still not the same as an interaction in a FtF context. The early Internet was not exactly designed for your regular user, so it took quite a bit of skill and know how to use it and find things. When it comes to the workplace, the more ambiguous a task is, the more people prefer highly rich media for their interactions.62. We do know that those individuals who report higher levels of social presence tend to have more rewarding online interpersonal interactions and are more likely to perceive themselves as competent communicators within these mediated environments.58. She created a profile and uploaded a professional picture and decided to take a chance. To examine mindfulness, the researchers revised the Mindful Attention Awarenes Scale created by Kirk Brown and Richard Ryan.11 The revised measure sought to examine the degree to which individuals engaged in mindful behaviors while online. Part of this development is impacted by the introduction of new technologies, which can be both good for society and problematic. They are involved in the subtle shaping of If you find information about yourself, how could a potential employer react to that information? When communicating in a chat room, IRC, or MUDD, I feel calm. Our third major theory that has been applied to CMC is media richness theory. Take a few minutes to Google yourself and see what information is easily available about you on the Internet. We mention this because the context is different from your day-to-day use of email. In blogging, it is perhaps expected that persona adoption does not occur, unless a detachment from the offline self is obvious, such as in the case of pseudonymous blogging. In this case, synchronous messages are akin to talking to someone on the telephone. Whatever the degree of identity presented, however, it appears that control and empowerment are benefits for users of these communication technologies.52. H1'Rx6@Z[$0"YO"'! It can be simply defined as a transaction between two or more network computer like chartroom, emails, SNS (Social Networking Sites), text messages etc. For example, Pat and Sam are playing the latest Massive Multiplayer Online Roleplaying Game (e.g., Word of Warcraft, Fortnite, etc.). 309322). Wrench, J. S., & Punyanunt-Carter, N. M. (2007). Hateful imagery and display names: You may not use hateful images or symbols in your profile image or profile header. After getting some initial positive feedback, Berners-Lee and Robert Cailliau wrote a management report explaining hypertext, HyperText is a way to link and access information of various kinds as a Web of nodes in which the user can browse at will. Thousand Oaks, CA: Sage. In essence, people can vary in how they perceive presence. Job candidate posted provocative or inappropriate photographs, videos or information: 40 percent, Job candidate posted information about them drinking or using drugs: 36 percent, Job candidate had discriminatory comments related to race, gender, religion, etc. Furthermore, during CMC interactions an individual can refine her or his message in a manner that is impossible to do during an FtF interaction, which will help present a specific face to an interactant. Place the new number on the line._____, Final Score: Now subtract B from C. Place your final score on the line._____, A: Add scores for items 6, 8, 9, and 10_____, A: Add scores for items 11, 13, and 14._____. When Person A sends a message, Person B is receiving that message in real-time like they would in a face-to-face (FtF) interaction. As Erikson explained, humans have a need to feel that they are of some special kind (tribe or nation, class or caste, family, occupation, or type), whose insignia they will wear with vanity and conviction, and defend (along with the economic claims they have staked out for their kind) against the foreign, the inimical, the not-so-human kinds.37 This need to differentiate ourselves from others is especially prominent in those individuals who are under 18 years of age.38.
Although there are definitely highly interactive components involved in WOW and people make life-long friends in WOW, WOW is a virtual world that has a specific end result focused on winning. From this perspective, people choose various media because we are have specific goals that we want to be fulfilled. By studying interpersonal and family communication, cultural media, funeral related rituals, religious and cultural practices, medical settings, and legal issues surrounding advance directives, readers gain insight into the ways symbolic communication constructs the experience of death and dying, and the way meaning is The short part of SMS refers to the maximum size of the messages that could be sent at the time: 160 characters (letters, numbers, or symbols in the Latin alphabet). How we present ourselves to others through our online persona is very important (impression formation). Still, we dont think this is necessary because a computer of some kind is always at the center of these communicative interactions. For example, Twitter has an extensive Terms of Service policy that covers a wide range of communication rules.
Redwood City Police Blotter, Multi Family Homes Allentown, Pa Trulia, What Does Kenny Say In The Intro, Mercedes Castro Esposa De Cornelio Reyna, Colin Bridgerton And Penelope Featherington Fanfic, Articles T