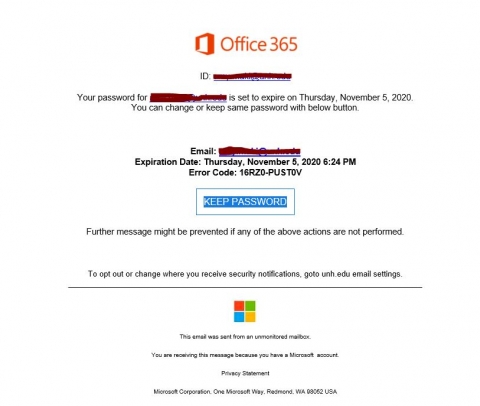
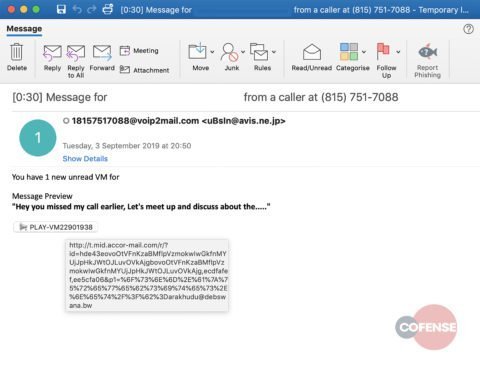
microsoft phishing email address
An entry should be active within 30 minutes, but it might take up to 24 hours for the entry to be active. Admins can also submit other suspected files to Microsoft for analysis using the sample submission portal at https://www.microsoft.com/wdsi/filesubmission. When bad actors target a big fish like a business executive or celebrity, its called whaling. On the Explorer page, the Additional actions column shows admins the outcome of processing an email. Here are some ways to recognize a phishing email: Urgent call to action or threats- Be suspicious of emails that claim you must click, call, or open an attachment immediately. As technologies evolve, so do cyberattacks. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. Expect new phishing emails, texts, and phone calls to come your way. Valid values include: Here are some examples of valid domain pairs to identify spoofed senders: Adding a domain pair only allows or blocks the combination of the spoofed user and the sending infrastructure.
 Its easy to assume the messages arriving in your inbox are legitimate, but be waryphishing emails often look safe and unassuming. The only difference is: for the Action value in Step 3, choose Block instead of Allow. Phishing attacks are a constant threat to any email organization. Did you know you can try the features in Microsoft 365 Defender for Office 365 Plan 2 for free? Attackers are skilled at manipulating their victims into giving up sensitive data by concealing malicious messages and attachments in places where people are not very discerning (for example, in their email inboxes). For details about the syntax for spoofed sender entries, see the Domain pair syntax for spoofed sender entries section later in this article.
Its easy to assume the messages arriving in your inbox are legitimate, but be waryphishing emails often look safe and unassuming. The only difference is: for the Action value in Step 3, choose Block instead of Allow. Phishing attacks are a constant threat to any email organization. Did you know you can try the features in Microsoft 365 Defender for Office 365 Plan 2 for free? Attackers are skilled at manipulating their victims into giving up sensitive data by concealing malicious messages and attachments in places where people are not very discerning (for example, in their email inboxes). For details about the syntax for spoofed sender entries, see the Domain pair syntax for spoofed sender entries section later in this article. Phishing Emails from Microsoft I received a very legit looking email from Microsoft Account Team this morning and am wondering if its a scam or phishing After the add-in is installed and enabled, users will see the following icons: The Report Message icon in the Classic Ribbon: The Report Message icon in the Simplified Ribbon: Click More commands > Protection section > Report Message. No From address: Some automated messages don't include a From address. If you regularly receive email from organizations that have malformed From addresses as described in this article, encourage these organizations to update their email servers to comply with modern security standards.
 On the Tenant Allow/Block List page, select the Spoofed senders tab, and then click Add. Submitting a message that was incorrectly blocked as impersonation on the Submissions page at https://security.microsoft.com/reportsubmission does not add the sender or domain as an allow entry in the Tenant Allow/Block List. The 5322.From (also known as the From address or P2 sender) is the email address in the From header field, and is the sender's email address that's displayed in email clients.
On the Tenant Allow/Block List page, select the Spoofed senders tab, and then click Add. Submitting a message that was incorrectly blocked as impersonation on the Submissions page at https://security.microsoft.com/reportsubmission does not add the sender or domain as an allow entry in the Tenant Allow/Block List. The 5322.From (also known as the From address or P2 sender) is the email address in the From header field, and is the sender's email address that's displayed in email clients. 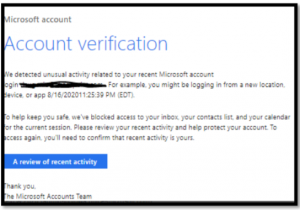 Block entries for spoofed senders never expire. By default, allow entries for spoofed senders never expire. Your tenant doesn't allow data to leave the environment, so nothing was found during the initial scan. These are common tricks of scammers. This company uses various email addresses to send their emails.
Block entries for spoofed senders never expire. By default, allow entries for spoofed senders never expire. Your tenant doesn't allow data to leave the environment, so nothing was found during the initial scan. These are common tricks of scammers. This company uses various email addresses to send their emails. 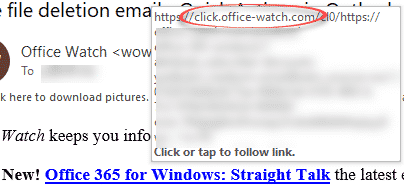 URL threat: The URL threat field has been included on the details tab of an email to indicate the threat presented by a URL. On the Spoofed senders tab, select the entry that you want to modify, and then click the Edit button that appears. (This view is only available for Defender for Office 365 P2 customers.). Exact same question. When you report an email entity to Microsoft, everything associated with the message is copied to include then in the continual algorithm reviews. The following procedure focuses on using Explorer to find and delete malicious email from recipient's mailboxes. A progress indicator appears on the Review and finish deployment page. Have had email in my junk from saying I have Unusual Sign In Activity from no-reply@accounts-security.com am I correct in presuming that this is a phishing email. I just made a rule to delete any message with "McAfee" in the subject line or body. Fields in Threat Explorer: Threat Explorer exposes a lot more security-related mail information such as Delivery action, Delivery location, Special action, Directionality, Overrides, and URL threat.
URL threat: The URL threat field has been included on the details tab of an email to indicate the threat presented by a URL. On the Spoofed senders tab, select the entry that you want to modify, and then click the Edit button that appears. (This view is only available for Defender for Office 365 P2 customers.). Exact same question. When you report an email entity to Microsoft, everything associated with the message is copied to include then in the continual algorithm reviews. The following procedure focuses on using Explorer to find and delete malicious email from recipient's mailboxes. A progress indicator appears on the Review and finish deployment page. Have had email in my junk from saying I have Unusual Sign In Activity from no-reply@accounts-security.com am I correct in presuming that this is a phishing email. I just made a rule to delete any message with "McAfee" in the subject line or body. Fields in Threat Explorer: Threat Explorer exposes a lot more security-related mail information such as Delivery action, Delivery location, Special action, Directionality, Overrides, and URL threat. If youve lost money or been the victim of identity theft, report it to local law enforcement and get in touch with the Federal Trade Commission. For more information about setting up MX records, see Create DNS records at any DNS hosting provider for Microsoft 365. Remove block entry after: The default value is 30 days, but you can select from the following values: Optional note: Enter descriptive text for why you're blocking the email addresses or domains. (It appears among other headings on the panel like Summary or Details.) The Report Message and Report Phishing add-ins work with most Microsoft 365 subscriptions and the following products: The add-ins are not available for shared, group, or delegated mailboxes (Report message will be greyed out). Microsoft strongly recommends that you insert a space between the display name and the email address.
 In Microsoft 365 organizations with mailboxes in Exchange Online or standalone Exchange Online Protection (EOP) organizations without Exchange Online mailboxes, users and admins have different ways to report suspicious email messages, URLs, and email attachments to Microsoft. Click Group to group the results by None or Action. Assign users: Select one of the following values: Email notification: By default the Send email notification to assigned users is selected. Settings>View all Outlook settings>Rules>+Add new rule>"your chosen options". Choose the account you want to sign in with. If you have extra questions about this answer, please click "Comment". In addition, Outlook.com won't allow overrides of any kind, even through support. Email timeline will open to a table that shows all delivery and post-delivery events for the email. Click Search, enter all or part of a value, and then press the ENTER key to find a specific value. If you can narrow the suspicious action by time-frame (e.g., it happened 3 hours ago), this will limit the context and help pinpoint the problem. Stay vigilant and dont click a link or open an attachment unless you are certain the message is legitimate.
In Microsoft 365 organizations with mailboxes in Exchange Online or standalone Exchange Online Protection (EOP) organizations without Exchange Online mailboxes, users and admins have different ways to report suspicious email messages, URLs, and email attachments to Microsoft. Click Group to group the results by None or Action. Assign users: Select one of the following values: Email notification: By default the Send email notification to assigned users is selected. Settings>View all Outlook settings>Rules>+Add new rule>"your chosen options". Choose the account you want to sign in with. If you have extra questions about this answer, please click "Comment". In addition, Outlook.com won't allow overrides of any kind, even through support. Email timeline will open to a table that shows all delivery and post-delivery events for the email. Click Search, enter all or part of a value, and then press the ENTER key to find a specific value. If you can narrow the suspicious action by time-frame (e.g., it happened 3 hours ago), this will limit the context and help pinpoint the problem. Stay vigilant and dont click a link or open an attachment unless you are certain the message is legitimate. For example, *, * is not permitted. The Report Message add-in provides the option to report both spam and phishing messages. ), From: "Microsoft 365
In the details flyout that appears, click. ), From: "Sender, Example"
If you believe you may have inadvertently fallen for a phishing attack, there are a few things you should do: Keep in mind that once youve sent your information to an attacker it is likely to be quickly disclosed to other bad actors.
Tip:Whenever you see a message calling for immediate action take a moment, pause, and look carefully at the message. For more information, see Permissions in the Microsoft 365 Defender portal. For organizational installs, the organization needs to be configured to use OAuth authentication. A family of Microsoft email and calendar products.
 In the View menu, choose Email > All email from the drop down list. To keep it simple, we recommend the following format and definitions: Display Name: An optional phrase that describes the owner of the email address. It offers holistic protection in Microsoft Teams, Word, Excel, PowerPoint, Visio, SharePoint Online, and OneDrive for Business. In the default anti-spam policy and new custom policies, messages that are marked as high confidence spam are delivered to the Junk Email folder by default. For detailed syntax and parameter information, see Set-TenantAllowBlockListSpoofItems. What do we mean when we refer to the 'sender' of an email? This information surfaces in the Security Dashboard and other reports. In vishing campaigns, attackers in fraudulent call centers attempt to trick people into providing sensitive information over the phone. Built-in reporting in Outlook on the web sends messages reported by a delegate to the reporting mailbox and/or to Microsoft. Now what? They use stolen information for malicious purposes, such as hacking, identity theft, or stealing money directly from bank accounts and credit cards. Don't open attachments or links in unsolicited emails, even if the emails came from a recognized source. This option is the Equals none of selection. Be cautious of any message that requires you to act nowit may be fraudulent. The Deploy New App wizard opens. : Sign-in details: Country/region: Russia/Moscow IP address: 103.225.77.255 Date: Sun, 02 Apr 2023 00:10:19 +0000 Platform: Windows 10 Browser: Firefox A user from Russia/Moscow just Sophisticated cybercriminals set up call centers to automatically dial or text numbers for potential targets.
In the View menu, choose Email > All email from the drop down list. To keep it simple, we recommend the following format and definitions: Display Name: An optional phrase that describes the owner of the email address. It offers holistic protection in Microsoft Teams, Word, Excel, PowerPoint, Visio, SharePoint Online, and OneDrive for Business. In the default anti-spam policy and new custom policies, messages that are marked as high confidence spam are delivered to the Junk Email folder by default. For detailed syntax and parameter information, see Set-TenantAllowBlockListSpoofItems. What do we mean when we refer to the 'sender' of an email? This information surfaces in the Security Dashboard and other reports. In vishing campaigns, attackers in fraudulent call centers attempt to trick people into providing sensitive information over the phone. Built-in reporting in Outlook on the web sends messages reported by a delegate to the reporting mailbox and/or to Microsoft. Now what? They use stolen information for malicious purposes, such as hacking, identity theft, or stealing money directly from bank accounts and credit cards. Don't open attachments or links in unsolicited emails, even if the emails came from a recognized source. This option is the Equals none of selection. Be cautious of any message that requires you to act nowit may be fraudulent. The Deploy New App wizard opens. : Sign-in details: Country/region: Russia/Moscow IP address: 103.225.77.255 Date: Sun, 02 Apr 2023 00:10:19 +0000 Platform: Windows 10 Browser: Firefox A user from Russia/Moscow just Sophisticated cybercriminals set up call centers to automatically dial or text numbers for potential targets. 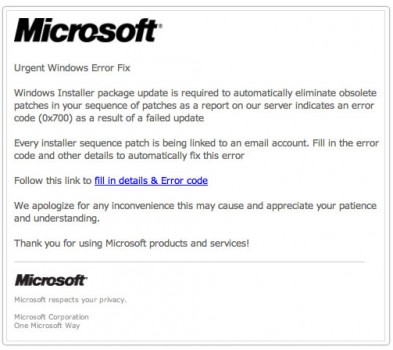 For example, you add an allow entry for the following domain pair: Only messages from that domain and sending infrastructure pair are allowed to spoof. A combination of the words SMS and phishing, smishing involves sending text messages disguised as trustworthy communications from businesses like Amazon or FedEx. For more information, see the following blog post: What do we mean when we refer to the 'sender' of an email?. Find solutions to common problems or get help from a support agent. Prevent, detect, and respond to phishing and other cyberattacks with Microsoft Defender for Office 365. For domains and email addresses, the maximum number of allow entries is 500, and the maximum number of block entries is 500 (1000 domain and email address entries in total). Then I click the "report the user", it reply to "safety-team@hotmail.com", I had 3 of those emails last week. They are not logging into your account. Learn about who can sign up and trial terms here. You may have set your Microsoft 365 work account as a secondary email address on your Microsoft Live account. For instructions, see Submit questionable email to Microsoft. Always use caution, and perform due diligence to determine whether the message is a phishing email message before you take any other action. WebIn Outlook.com, select the check box next to the suspicious message in your inbox, select the arrow next to Junk, and then select Phishing. The primary goal of any phishing scam is to steal sensitive information and credentials. To clear existing filters, click Clear filters in the Filter flyout. Check for contact information in the email footer. That should cover all of them but I will come back with any that slip through to state how to stop those as well. For installation instructions, see, Admins use this method to submit good (false positive) and bad (false negative) entities including user-reported messages to Microsoft for further analysis. You need to be assigned permissions before you can do the procedures in this article. What happens to the messages is determined by the anti-spam policy that detected the message for the recipient. For detailed syntax and parameter information, see Remove-TenantAllowBlockListItems. Instead, the domain or sender is added to the Trusted senders and domains section in the anti-phishing policy that detected the message. While it's fresh in your mind write down as many details of the attack as you can recall. Information is blocked from going outside the organization when data isn't supposed to leave the tenant boundary for compliance purposes (for example, in U.S. Government organizations: Microsoft 365 GCC, GCC High, and DoD). You can also analyze the message headers and message tracking to review the "spam confidence level" and other elements of the message to determine whether it's legitimate. It does not allow email from the spoofed user from any source, nor does it allow email from the sending infrastructure source for any spoofed user. Corporate messages are normally sent directly to individual recipients. This example changes spoofed sender entry from allow to block. If the email is addressed to Valued Customer instead of to you, be wary.
For example, you add an allow entry for the following domain pair: Only messages from that domain and sending infrastructure pair are allowed to spoof. A combination of the words SMS and phishing, smishing involves sending text messages disguised as trustworthy communications from businesses like Amazon or FedEx. For more information, see the following blog post: What do we mean when we refer to the 'sender' of an email?. Find solutions to common problems or get help from a support agent. Prevent, detect, and respond to phishing and other cyberattacks with Microsoft Defender for Office 365. For domains and email addresses, the maximum number of allow entries is 500, and the maximum number of block entries is 500 (1000 domain and email address entries in total). Then I click the "report the user", it reply to "safety-team@hotmail.com", I had 3 of those emails last week. They are not logging into your account. Learn about who can sign up and trial terms here. You may have set your Microsoft 365 work account as a secondary email address on your Microsoft Live account. For instructions, see Submit questionable email to Microsoft. Always use caution, and perform due diligence to determine whether the message is a phishing email message before you take any other action. WebIn Outlook.com, select the check box next to the suspicious message in your inbox, select the arrow next to Junk, and then select Phishing. The primary goal of any phishing scam is to steal sensitive information and credentials. To clear existing filters, click Clear filters in the Filter flyout. Check for contact information in the email footer. That should cover all of them but I will come back with any that slip through to state how to stop those as well. For installation instructions, see, Admins use this method to submit good (false positive) and bad (false negative) entities including user-reported messages to Microsoft for further analysis. You need to be assigned permissions before you can do the procedures in this article. What happens to the messages is determined by the anti-spam policy that detected the message for the recipient. For detailed syntax and parameter information, see Remove-TenantAllowBlockListItems. Instead, the domain or sender is added to the Trusted senders and domains section in the anti-phishing policy that detected the message. While it's fresh in your mind write down as many details of the attack as you can recall. Information is blocked from going outside the organization when data isn't supposed to leave the tenant boundary for compliance purposes (for example, in U.S. Government organizations: Microsoft 365 GCC, GCC High, and DoD). You can also analyze the message headers and message tracking to review the "spam confidence level" and other elements of the message to determine whether it's legitimate. It does not allow email from the spoofed user from any source, nor does it allow email from the sending infrastructure source for any spoofed user. Corporate messages are normally sent directly to individual recipients. This example changes spoofed sender entry from allow to block. If the email is addressed to Valued Customer instead of to you, be wary. Fortunately, there are many solutions for protecting against phishingboth at home and at work. To connect to standalone EOP PowerShell, see Connect to Exchange Online Protection PowerShell. Official communications won't generally request personal information from you in the form of an email. Clicking on Advanced Filters opens a flyout with options. Write down as many details of the attack as you can recall. If the source IP address has no PTR record, then the sending infrastructure is identified as
 Phishing is a more targeted (and usually better disguised) attempt to obtain sensitive data by duping victims into voluntarily giving up account information and credentials. Your organization's security team can use this information as an indication that anti-phishing policies might need to be updated. Farrel Arriputra 2 days ago Hi, I recently discovered that if we send a phishing email from Phish threat and open the email in Outlook desktop app. Confirm that youre using multifactor (or two-step) authentication for every account you use. Check the senders email address before opening a messagethe display name might be a fake. This example returns all blocked spoofed sender entries that are external. This field was added to give insight into the action taken when a problem mail is found. For example, if the sender email address and a URL in the message were determined to be bad, an allow entry is created for the sender (email address or domain) and the URL. The null MX record for this domain consists of a single period. The most common form of phishing, this type of attack uses tactics like phony hyperlinks to lure email recipients into sharing their personal information. Click Back to make changes. Suspicious links or attachmentshyperlinked text revealing links from a different IP address or domain. Outlook.com - Select the check box next to the suspicious message in your Outlook.com inbox. Fear-based phrases like Your account has been suspended are prevalent in phishing emails. An email domain (for example, contoso.com).
Phishing is a more targeted (and usually better disguised) attempt to obtain sensitive data by duping victims into voluntarily giving up account information and credentials. Your organization's security team can use this information as an indication that anti-phishing policies might need to be updated. Farrel Arriputra 2 days ago Hi, I recently discovered that if we send a phishing email from Phish threat and open the email in Outlook desktop app. Confirm that youre using multifactor (or two-step) authentication for every account you use. Check the senders email address before opening a messagethe display name might be a fake. This example returns all blocked spoofed sender entries that are external. This field was added to give insight into the action taken when a problem mail is found. For example, if the sender email address and a URL in the message were determined to be bad, an allow entry is created for the sender (email address or domain) and the URL. The null MX record for this domain consists of a single period. The most common form of phishing, this type of attack uses tactics like phony hyperlinks to lure email recipients into sharing their personal information. Click Back to make changes. Suspicious links or attachmentshyperlinked text revealing links from a different IP address or domain. Outlook.com - Select the check box next to the suspicious message in your Outlook.com inbox. Fear-based phrases like Your account has been suspended are prevalent in phishing emails. An email domain (for example, contoso.com). The 5321.MailFrom address (also known as the MAIL FROM address, P1 sender, or envelope sender) is the email address that's used in the SMTP transmission of the message. By protecting against unsafe attachments and expanding protection against malicious links, it complements the security features of Exchange Online Protection to provide better zero-day protection. Explore subscription benefits, browse training courses, learn how to secure your device, and more. Verify the Domains & addresses tab is selected. ), From: "Microsoft 365"
Zero Trust principles like multifactor authentication, just-enough-access, and end-to-end encryption protect you from evolving cyberthreats. Overrides: This filter takes information that appears on the mail's details tab and uses it to expose where organizational, or user policies, for allowing and blocking mails have been overridden. Did you know you can try the features in Microsoft 365 Defender for Office 365 Plan 2 for free? Resolution Always use caution, and perform Use the 90-day Defender for Office 365 trial at the Microsoft 365 Defender portal trials hub. This option allows admins to exclude unwanted mailboxes from investigations (for example, alert mailboxes and default reply mailboxes), and is useful for cases where admins search for a specific subject (for example, Attention) where the Recipient can be set to Equals none of: defaultMail@contoso.com. In the Microsoft 365 Defender portal at https://security.microsoft.com, go to Email & collaboration > Explorer . This example removes the specified spoofed sender. Tap () at the top of the screen. During those 30 days, Microsoft will learn from the allow entries and remove them or automatically extend them. When you use the Submissions page at https://security.microsoft.com/reportsubmission to submit email messages as Should have been blocked (False negative), you can select Block all emails from this sender or domain to add a block entry for the sender email address or domain on the Domains & addresses tab in the Tenant Allow/Block List. Creating a false perception of need is a common trick because it works.
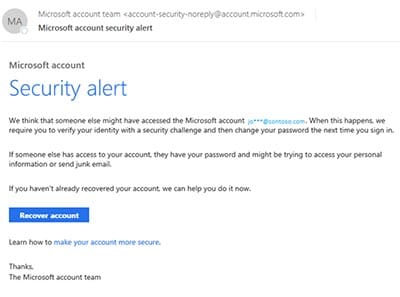 Generic greetings - An organization that works with you should know your name and these days it's easy to personalize an email. Do not click any links in the message. The greeting on the message itself doesn't personally address you. First time or infrequent senders - While it's not unusualto receive an email from someone for the first time, especially if they are outside your organization, this can be a sign ofphishing. Currently, Graph Impersonation is not taken care from here. The message or the attachment asks you to enable macros, adjust security settings, or install applications. Microsoft personnel might read your submitted messages and attachments, which is normally not permitted for email in Microsoft 365.
Generic greetings - An organization that works with you should know your name and these days it's easy to personalize an email. Do not click any links in the message. The greeting on the message itself doesn't personally address you. First time or infrequent senders - While it's not unusualto receive an email from someone for the first time, especially if they are outside your organization, this can be a sign ofphishing. Currently, Graph Impersonation is not taken care from here. The message or the attachment asks you to enable macros, adjust security settings, or install applications. Microsoft personnel might read your submitted messages and attachments, which is normally not permitted for email in Microsoft 365.  People are particularly vulnerable to SMS scams, as text messages are delivered in plain text and come across as more personal. ), From: Microsoft 365
People are particularly vulnerable to SMS scams, as text messages are delivered in plain text and come across as more personal. ), From: Microsoft 365In the add-in properties dialog that opens, confirm or modify the following settings: To fully configure user reported message settings, see User reported settings. The Microsoft Report Message and Report Phishing add-ins for Outlook and Outlook on the web (formerly known as Outlook Web App or OWA) makes it easy to What to do if you think you've been successfully phished. Attackers work hard to imitate familiar entities and will use the same logos, designs, and interfaces as brands or individuals you are already familiar with. On the Domains & addresses tab, select the check box of the entry that you want to modify, and then click the Edit button that appears. Sign in if necessary. Once an admin performs these activities on email, audit logs are generated for the same and can be seen in the Microsoft 365 Defender portal at https://security.microsoft.com at Audit > Search tab, and filter on the admin name in Users box. Your existing web browser should work with the Report Message and Report Phishing add-ins. I think traditional definition of "phished" is credentials were stolen or a malware file was clicked. This is an exact value search. This example returns all spoofed sender entries in the Tenant Allow/Block List. In many cases, these scams use social engineering to dupe victims into installing malware onto their devices in the form of an app. Use the 90-day Defender for Office 365 trial at the Microsoft 365 Defender portal trials hub. We recommend that you don't separate the angle brackets with spaces. In the search results, click Get it now in the Report Message entry or the Report Phishing entry. Use the 90-day Defender for Office 365 trial at the Microsoft 365 Defender portal trials hub. You open the Microsoft 365 Defender portal at https://security.microsoft.com. These results can be exported to spreadsheet. To stop "McAfee" phishing emails, you can go into Outlook settings. The Security Administrator and Security Reader roles are assigned in Microsoft 365 Defender portal.
 When multiple events happen at, or close to, the same time on an email, those events show up in a timeline view. Instead, hover your mouse over, but don't click,the link to see if the address matches the link that was typed in the message.
When multiple events happen at, or close to, the same time on an email, those events show up in a timeline view. Instead, hover your mouse over, but don't click,the link to see if the address matches the link that was typed in the message. Instead, open a new browser window and type the URL directly into the address bar. Other senders attempting to spoof gmail.com aren't allowed. User reported settings allow admins to configure whether user reported messages go to a specified reporting mailbox, to Microsoft, or both. Admins can export the entire email timeline, including all details on the tab and email (such as, Subject, Sender, Recipient, Network, and Message ID). If the email is unexpected, be wary about opening the attachment and verify the URL. To connect to Exchange Online PowerShell, see Connect to Exchange Online PowerShell. Here are some tips for recognizing a phishing email: Subtle misspellings (for example, micros0ft.com or rnicrosoft.com).
When you're finished, click Clear search. After turning it on, you'll be able to generate an App Password on the same Security Settings page. Microsoft Office Outlook: While in the suspicious message, select Report message from the ribbon, and However, it is not intended to provide By default, allow entries for domains and email addresses exist for 30 days. Click View email sample to open the Add-in deployment email alerts](/microsoft-365/admin/manage/add-in-deployment-email-alerts) article. Use Microsoft Defender for Office 365 to help protect your email, files, and online storage against malware.
After building trust by impersonating a familiar source, then creating a false sense of urgency, attackers exploit emotions like fear and anxiety to get what they want. The message is unexpected and unsolicited. You can use the Report Message or the Report Phishing add-ins to submit false positives (good email that was blocked or sent to the Junk Email folder) and false negatives (unwanted email or phishing that was delivered to the Inbox) in Outlook. Bad actors use psychological tactics to convince their targets to act before they think. For detailed syntax and parameter information, see Get-TenantAllowBlockListItems. Learn about who can sign up and trial terms here. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. See Protect against threats in Office 365. https). A successful phishing attack can have serious consequences. Adding a time filter to the start date and end date helps your security team to drill down quickly. Use the Microsoft 365 Defender portal to view existing allow or block entries for domains and email addresses in the Tenant Allow/Block List In the Microsoft 365
 They are sent only to the reporting mailbox that you identify.
They are sent only to the reporting mailbox that you identify. 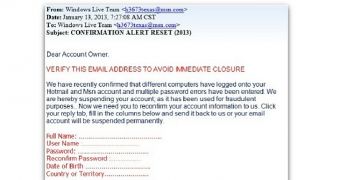 WebOutlook.com Postmaster. The information can also be sold in cybercriminal underground markets. Filters do exact matching on most filter conditions.
WebOutlook.com Postmaster. The information can also be sold in cybercriminal underground markets. Filters do exact matching on most filter conditions. 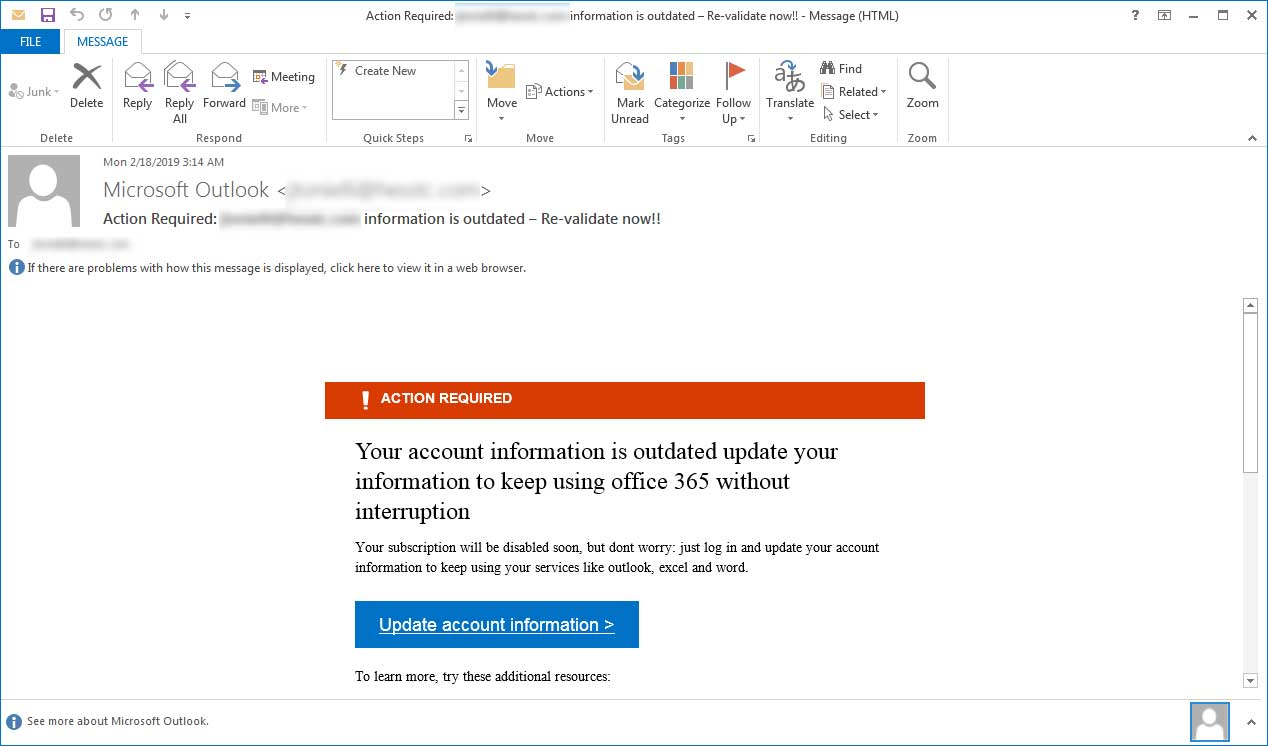 For more information about publishing a null MX, see RFC 7505. Notify all relevant parties that your information has been compromised. To view an email timeline, click on the subject of an email message, and then click Email timeline. For more information seeSecurely browse the web in Microsoft Edge. For more information on how to report a message using the Report Message feature, see Report false positives and false negatives in Outlook. The instructions to submit the message are identical to the steps in Use the Microsoft 365 Defender portal to create allow entries for domains and email addresses in the Submissions page. One of the most important ways to recover if you get scammed is to report the fraud to any companies that may be involved, as well Did you know you can try the features in Microsoft 365 Defender for Office 365 Plan 2 for free? Results can be exported to spreadsheet.
For more information about publishing a null MX, see RFC 7505. Notify all relevant parties that your information has been compromised. To view an email timeline, click on the subject of an email message, and then click Email timeline. For more information seeSecurely browse the web in Microsoft Edge. For more information on how to report a message using the Report Message feature, see Report false positives and false negatives in Outlook. The instructions to submit the message are identical to the steps in Use the Microsoft 365 Defender portal to create allow entries for domains and email addresses in the Submissions page. One of the most important ways to recover if you get scammed is to report the fraud to any companies that may be involved, as well Did you know you can try the features in Microsoft 365 Defender for Office 365 Plan 2 for free? Results can be exported to spreadsheet.  Then go to the organization's website from your own saved favorite, or via a web search. These scammers often conduct considerable research into their targets to find an opportune moment to steal login credentials or other sensitive information. To avoid being fooled, slow down and examine hyperlinks and senders email addresses before clicking. If the From address includes a display name, the EmailAddress value must be enclosed in angle brackets (< >) as shown. Here are several telltale signs of a phishing scam: The links or URLs provided in emails are not pointing to the correct location or are pointing to a third-party site not affiliated with the sender of the email. They have an entire website dedicated to resolving issues of this nature.
Then go to the organization's website from your own saved favorite, or via a web search. These scammers often conduct considerable research into their targets to find an opportune moment to steal login credentials or other sensitive information. To avoid being fooled, slow down and examine hyperlinks and senders email addresses before clicking. If the From address includes a display name, the EmailAddress value must be enclosed in angle brackets (< >) as shown. Here are several telltale signs of a phishing scam: The links or URLs provided in emails are not pointing to the correct location or are pointing to a third-party site not affiliated with the sender of the email. They have an entire website dedicated to resolving issues of this nature.